AES (Advanced Encryption Standard)
AES is a block of cipher algorithms originating from Rijndael algorithms (from the surnames of its inventors, two Belgian cryptographers: Joan Daemen and Vincent Rijmen).
Currently, the telephone cryptographic applications provided by Kryptotel use this algorithm with a TOP SECRET 256-bit key.
This algorithm has been chosen because of its very high security levels and performance combined with its rapidity of calculation.
The following criterias have inspired the creators of this algorithm:
- High strength level of the algorithm: able to resist all different types of attacks;
- Rapidity of calculation and code compactness on a large number of platforms;
- Simplicity and transparency of the project.
It’s an open source algorithm that in 2001 was also adopted by NIST (National Institute of Standards and Technology), the U.S. Institute of Standardization, as the communication encryption standard for the U.S. and its federal agencies.
Following are the evaluation criteria that were used by NIST during the selection process:
- Security
- Maximum applicability
- High Software and Hardware Performance
- Eligibility to work in restricted environments
- Resistance to power analysis and other attacks
- Intellectual Property
- Equity
- Objectivity
- Flexibility
- Efficiency
After a five year standardization process the algorithm selection process led to a selection of 15 algorithms. A second selection, performed by NIST’s technical team, identified the five final algorithms: MARS, RC6TM, AES, Serpent, Twofish.
Finally, after years of reports and tests AES algorithm was chosen as the best authentication algorithm. NIST gives priority to the AES algorithm, because in case of brute force attack, the AES has a very high resistance to both small and large size systems, and it increases with the number of data and communications encrypted. For very large systems AES has proven to match RSA’s resistance.
It is a symmetric key encryption algorithm that encrypts a block of elements (set of bits) at the same time, unlike stream ciphers that encode each single item individually. This feature allows the algorithm to be very fast, up to 6 times faster than DES, and it is very versatile. In fact it is widely used for both hardware and software developments. It has the advantage of occupying very little memory and consequently makes it very suitable for low memory capacity devices like Smart cards. It maintains its performance for both key size variation and changing platforms.
The block cipher length is fixed at 128-bit, while encryption keys of this algorithm can be 128, 192 or 256 bits.
It’s in this aspect that AES differs from the Rijndael algorithm, which instead provides a block cipher length and key that must be a multiple of 32 bits with a minimum of 128 bits and a maximum of 256 bits.
But let’s see in detail how the algorithm works.
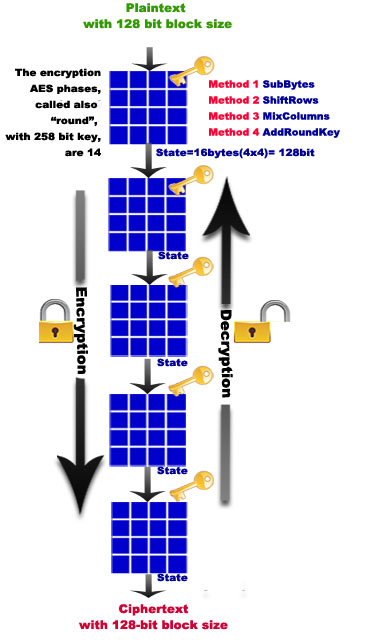
AES in order for it to work , being a 128-Bit Block cipher, needs to structure the plain text in matrices/blocks of 4 rows and 4 columns each (4×4 bytes = 128bit = 16bytes), which are called states ( “states”).
The AES encryption divides the encryption phase (“round”) in identical stages, each stage has its own session key or subkey that is extracted from the master key using the following process:
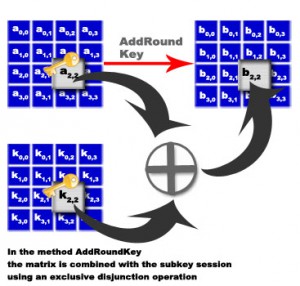
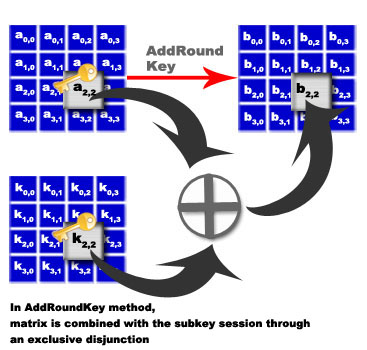
The AddRoundKey – Each byte of the block is encrypted with the session key, the session key is calculated from the key manager.
The number of stages changes at the variation of the key size in use, for example, there are 14 stages or rounds for a 256 bit encryption key .
Each phase consists of four methods that, applied to blocks (states), activate a series of operations that work to obtain the ciphertext:
- Method 1 SubBytes: each byte of the matrix is replaced with another in a non-linear way according to a specific table. It is this set of operations that gives the characteristics of the block cipher
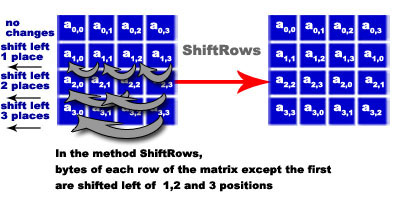
- Method 2 ShiftRows: bytes in each row are shifted cyclically by a certain offset, the number of places each byte is shifted differs for each row. It all takes place according to the line of provenience.
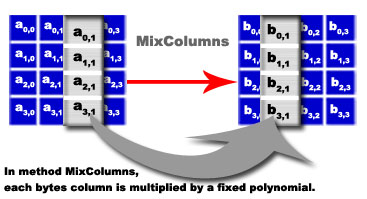
- Method 3 MixColumns: the bytes of each column are combined with a linear transformation.
- Method 4 AddRoundKey: each byte of the table is combined with a certain key.
All the encryption process can be summarized in the following steps: