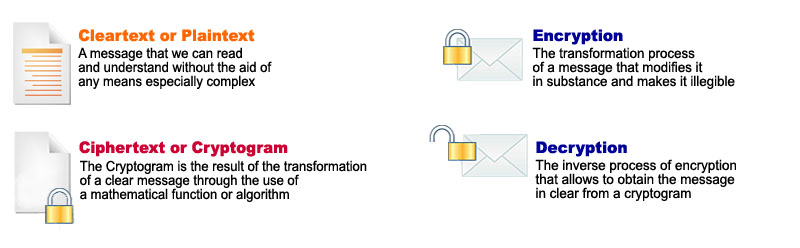
Cryptography or encryption is a technique used to keep information secret, limiting the access only to authorized people. A cipher is a system that allows to change a “plain text” (message), transforming it into a non-intelligible text (cipher-text or cryptogram).
Definitions
Encryption and Decryption Process
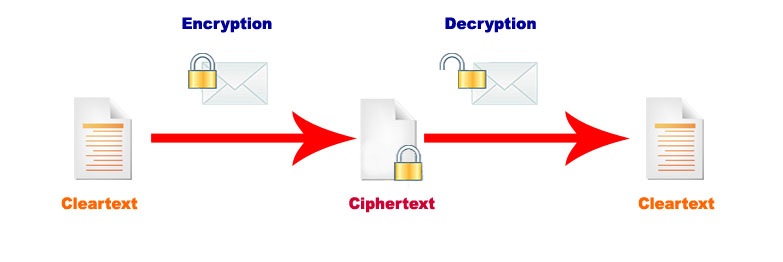
Encryption is the operation of transforming a message (referred to as plaintext) to a cryptogram, which is a set of symbols unreadable to anyone except those possessing the readable key. The transforming process must be reversible and allow, therefore, to reconstruct the previously encrypted message when the readable key is available. The encryption process takes place through the use of algorithms, complex mathematical functions that are applied to the message and make it unreadable without the decryption key. The encryption and decryption process can be described as follows:
The confidentiality and integrity of encrypted message is given by two factors:
- The strength of encryption algorithm.
- The secrecy of the encryption key.
The strength of an encryption algorithm is directly proportional to its computational complexity. The security of these systems, however, is given by the information sharing and technical specifications of the encryption algorithms in use. That’s why the “open source” philosophy is of vital importance in this field: the most important algorithms in use are those in public domain because are for their nature more reliable. It is a well-known fact that secret algorithms are the most insecure because transparency becomes synonymous with safety in cryptography. Kerckhoffs’ Principle: “A basic principle, adopted by all modern cryptographers, is that the algorithm which defines any cryptosystem must be publicly available. Only then is it possible for the cryptosystem to be subjected to peer review and critical analysis, so that users can have confidence in it”. This means that when a good encryption algorithm is used, the knowledge of the algorithm does not involve any kind of help unless the encryption / decryption key is known. It is therefore essential that the used encryption/decryption key must be hard to guess and be as long as possible, consequently the set of possible keys will be as long as possible. The cryptosystem is the encryption algorithm and the set of keys and protocols are what allow its operation.The cryptanalysis is the science that studies how to force a cryptographic system (cryptosystem). Cryptosystem is the package of all cryptographic algorithms and keys, procedures, protocols, and instructions used for encoding and decoding messages using cryptography. Most modern ciphers are still safe from cryptanalysis techniques. The attack on a cryptosystem has the goal of forcing the system. The method chosen and the danger depends on the information available to the cryptanalyst. Cryptanalysis Techniques There are several techniques used to force the system and give access to encrypted information
- Brute-Force, takes place calculating all the possible combinations of an encryption key. This technique, with the increase of more powerful computers, is becoming rapidly more effective.
- Differential cryptanalysis, analyzes the “distance” between the number of characters in the ciphertext using sophisticated mathematical techniques, combined with even faster algorithms.
- Man-in-the-middle, an attacker can be positioned between a sender and a recipient to exchange their private and public keys with others that have been accordingly modified.
Encryption Algorithms
There are different types of algorithms:
- Symmetric Algorithms
- Asymmetric or Public Key Algorithms
- Hybrid Algorithms
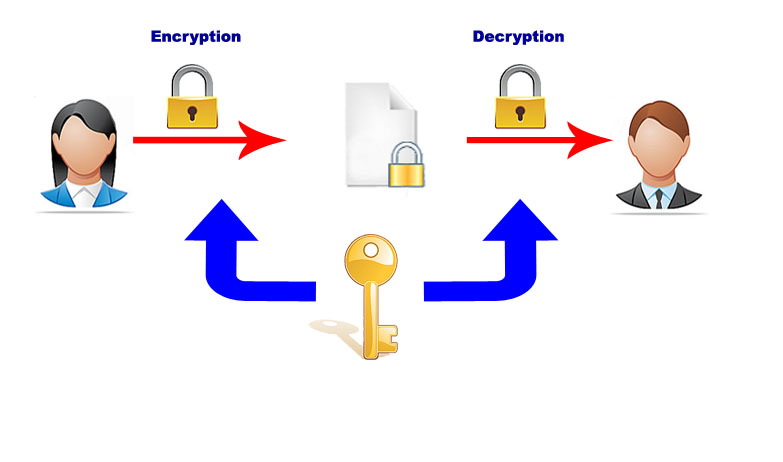
Symmetric Algorithms Symmetric algorithms (also called private-key encryption or secret-key encryption) involve using the same key for encryption and decryption. The most common private-key algorithms are DES (Data Encryption Standard), Triple-DES, Blowfish, IDEA and AES (Advanced Encryption Standard). Symmetric key systems have very long and strong keys but at the contrary are based on a single key for encryption and decryption with the risk of being intercepted during the key exchange between those involved in the process.
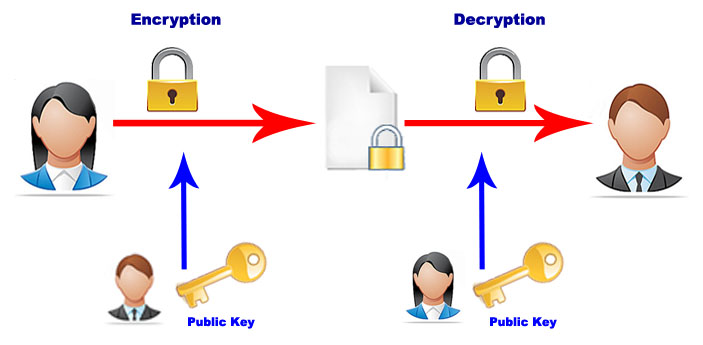
Asymmetric or Public Key Algorithms The public-key algorithms use two different keys to encrypt and decrypt the message. The keys are generated by a particular algorithm that doesn’t allow to obtain one key from another. One of the keys, called public key, is shared and will be used for the encryption process. The other key, called private, must be kept secret and is used to decrypt the messages. If person A wants to send a confidential message to the person B, for example, A encrypts the message with B’s public key, being a public key it is of public domain. This means that the message is decipherable only with B’s private key, being a private key, it can only be in B’s possession. The most common asymmetric key algorithms are RSA (named by their inventors: Rivest, Shamir and Adleman), Diffie-Hellman, DSS (Digital Signature Standard), Rabin, El Gamal, elliptic curve cryptography.
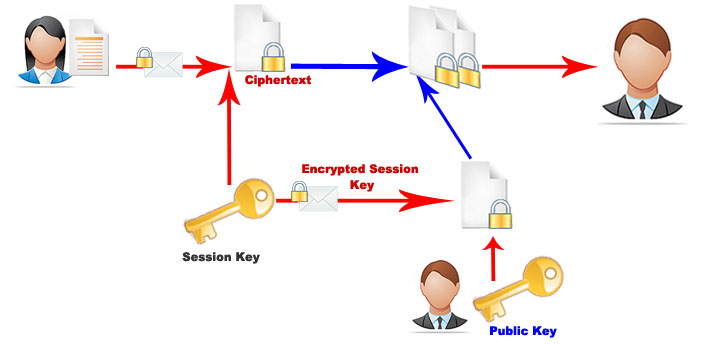
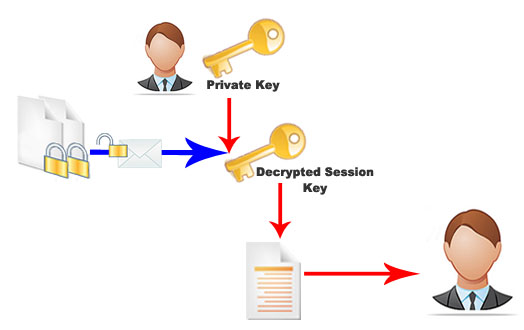
Hybrid Algorithms Usually asymmetric key systems ensure a good security level but are slower and computationally more demanding than symmetric key encryption. Hybrid Algorithms system uses a symmetric and an asymmetric public key system by combining the advantages of two systems: the safety of the public key and the speed of the symmetric key. Specifically the hybrid system uses a public key algorithm, usually RSA, in order to safely share the symmetric encryption system’s secret key. The real message is then encrypted using that key (usually DES because very fast) and then sent to the recipient. Since the key sharing method is secure, the symmetric key used for the encryption changes for each message sent. For this reason it is sometimes called the session key. This means that if the session key was intercepted, the interceptor would only be able to read the message encrypted with that key. In order to decrypt other messages the interceptor would have to intercept other session keys. The session key, encrypted using the public key algorithm, and the message being sent, encrypted with the symmetric algorithm, are automatically combined into a single package. The recipient uses his private key to decrypt the session key and then uses the session key to decrypt the message. Many applications use this system, the most popular are the PGP and GnuPG. Hybrid Encryption – Encoding process
Hybrid Encryption – Decoding process
Telephone Cryptography or Encryption
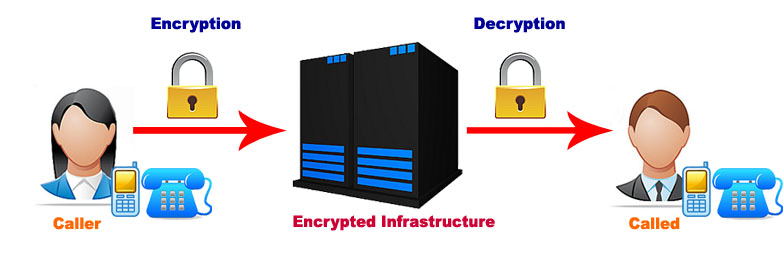
Cryptography, because of its features, has been largely developed in the last 30 years, and especially in the last decade due to the Internet phenomenon and the development of modern and faster communication techniques that are very insecure by nature (e-mail, landline and mobile communications). Encryption or cryptography in the internet and telecommunications era is a mathematical system that allows to encode or transform, through the use of algorithms, messages, phone calls and texts into not understandable symbols in a way that cannot be interpreted and understood by people not authorized to read or listen to them. Specifically, in the field of telephone conversations, cryptography encodes messages by altering the telephone signals and making them intelligible therefore not interpretable without a decryption key. Telephone encryption is widely used to protect conversations from the interception phenomenon. Interception is the activity of tapping communications, conversations, communication or telecommunication flows and different methods are used to do so.
Anti-interception methods
Telephone encryption applied to computers, landline and programmable mobile phones (smartphones), is the technique used to encrypt voice before sending it through to a data network (CSD GSM, PSTN, ISDN, UMTS, GPRS, HSDPA). An Encryption software is used and it works without interfering with the telco operator. It must be installed on the caller’s and recipient’s device. The encryption software works by creating a level of encryption through the use of certain algorithms or mathematical functions. An encryption algorithm (cipher) is a mathematical function used for the encryption/decryption process of communications. The algorithm works in conjunction with a key that is used to encode and decode the call.
Algorithms used in the telephony encryption
The most commonly used encryption system in the telecommunication field is the hybrid one. The most commonly used algorithms for land line and mobile telephony are a combination of the following: – AES (with 256-bit key)–>encryption key of the session key – RSA (with 4096 bit key pair) –>session key